What is statistical labeling?
Data labeling
Data labeling. In the system domain, statistical labeling is the system of identifying raw data (images, text files, videos, etc.) and adding one or more meaningful and informative labels to provide context so that a learning version of the device can learn from it. . For example, labels can indicate whether or not an image consists of a chicken or a car, what words were spoken in an audio recording, or whether an x-ray contains a tumor. Information tagging is necessary for an expansion of use cases such as computer vision, natural language processing, and speech reputation.
How does record tagging work?
Today, the most realistic knowledge acquisition models use supervised knowledge, which applies a set of rules to map an input to at least one output. For supervised learning of artworks, you need a ranked set of statistics that the model can analyze to make appropriate decisions. Fact labeling commonly begins by asking people to make judgments about a certain portion of unlabeled facts.
For example, taggers may be asked to tag all photographs in a data set where “photo contains a chicken” is true. Labeling can be as coarse as a simple yes or no or as granular as determining the precise pixels within the image related to the bird. The device that acquires knowledge of the model uses human-provided labels to learn the underlying patterns in a procedure known as “model training.” The end result is an educated version that can be used to make predictions about new statistics.
In technology data acquisition, a well-categorized data set that is used as a general target for training and testing a given model is often referred to as “core data.” The accuracy of your trained model will depend on the accuracy of your database, so it is essential to dedicate time and resources to ensure fairly accurate information labeling.
What are some common types of record labeling?
Imagination and Computer Vision When building a computer vision system, you must first label images, pixels, or key factors, or create a border that completely encloses a digital photograph, known as a bounding container, to generate your training data set. For example, you can classify photos by different type (such as product versus lifestyle images) or content (what’s actually inside the image), or you can split a photo at the pixel level. You can then use these educational records to build a computer vision model that can be used to automatically classify snapshots, find the location of elements, identify key points in an image, or slice a photograph.
Natural language processing
Natural language processing requires you to first manually perceive crucial sections of text or tag the text with specific tags to generate your school data set. For example, you may want to discover the sentiment or reason of a text blurb, understand elements of speech, classify proper nouns such as places and others, and find text in images, PDF files, or other documents. To do this, you can draw bounding containers around the text and then manually transcribe the text to your educational data set. Natural language processing models are used for sentiment analysis, entity name reputation, and optical person recognition.
Audio processing
Audio processing converts all types of sounds, such as speech, natural noises (barking, whistling, or squeaking), and construction sounds (breaking glass, scanning, or alarms) into a set format so they can be used in machine learning. . Audio processing often requires you to first manually transcribe it into written text content. From there, you can discover deeper data about the audio with the help of including tags and categorizing the audio. This categorized audio will become your school data set.
What are some quality practices for information labeling?
- There are numerous strategies to improve the efficiency and accuracy of record labeling. Some of these techniques include:
- Intuitive and optimized project interfaces to help limit cognitive load and context switching for human taggers.
- Labeler consensus to help counteract error/bias from male or female annotators. Labeler consensus involves sending each object in the data set to multiple annotators and then
- consolidate your answers (called “annotations”) into a single label.
- Label audit to verify label accuracy and replace as necessary.
- Energy domain to make statistical labeling more efficient by using devices to acquire knowledge to become aware of the most useful facts that can be classified by using humans.
How can information tagging be done effectively?
A successful system that masters models is built on the shoulders of large volumes of school statistics. However, how to create the educational statistics necessary to build these models is often expensive, complex, and time-consuming. Most models created today require a human to manually label information in a way that allows the model to learn to make accurate selections. To overcome this task, labeling can be made more efficient by using a version of device learning to label statistics automatically.
In this process, an automatic domain model is first educated to label information about a subset of raw data that has been classified by humans. Where the labeling model is highly confident in its consequences based on what it has learned so far, it will routinely apply labels to the raw data. In the event that the labeling version has less confidence in its results, it will overlook the facts for humans to perform the labeling.
The human-generated labels are then returned to the labeling version to learn and improve its ability to automatically label the next raw data set. Over the years, the version can tag more and more information robotically and significantly accelerate the arrival of educational data sets.
What is JSON (JavaScript Element Notation)?
JSON (JavaScript Element Notation) is a text-based, human-readable data exchange format used to exchange records between web users and web servers. The design defines hard and fast structuring rules for record-based representation. JSON is used as an opportunity for extensible markup language (XML).
JSON was initially based on the JavaScript programming language and was introduced as the page scripting language for the Netscape Navigator web browser. JSON is also occasionally used in server-side and computing device-side programming environments.
American laptop programmer Douglas Crockford created JSON. The design is derived from the well-known JavaScript programming language and follows the JavaScript object syntax. JSON includes element-name and punctuation pairs within the form of square brackets, parentheses, semicolons, and colons. Each item is described with an operator, including text or photo, and grouped with a cost to that operator. JSON files are classified as .json. JSON has a language-independent design.
JSON has a simple structure and does not use mathematical notation or algorithms. It is easy to understand, even for users with limited programming. It is considered a fast and accessible way to create interactive pages. It has become the format of the desire to have web services publicly available. It has local help in relational and NoSQL databases.
New JSON customers should be aware of the implications of capability protection, but. JSON scripts are routinely executed on any web page that a web browser requests. Therefore, they can be used to implement JavaScript injection attacks against a web user, such as a command injection or inline scripting to move a website.
For example, if a hacker inserts non-JSON code into a string, including a Trojan horse, the target ruleset executes the text as if it were JavaScript and then returns the cost of the remaining statement. If the only declaration is a JSON rate, there may be no effect. but, if a previous statement incorporates other JavaScript code, that code is executed by the script. This could give the hacker access to all the variables a script has access to, possibly compromising a person’s laptop.
Why is JSON used?
JSON became mainstream by using the global standardization standard such as ISO/IEC 21778:2017 in order to define the syntax of legitimate JSON texts.
JSON is used in JavaScript on the Internet as an opportunity for XML to organize data. JSON is language independent and can be combined with C++, Java, Python, and many different languages. Unlike XML, which is a full markup language, JSON is clearly a way of representing statistical systems. JSON files are quite lightweight and are created quickly on web servers.
A JSON JSON instance includes arrays and elements, as well as names and price pairs. Punctuation used within the format consists of quotation marks, parentheses, parentheses, semicolons, and colons.
The information in JSON is written in call and rate pairs, similar to the properties of JavaScript elements. A call and cost pair is constructed using a name that is placed in double costs, accompanied by a colon and a given rate.
For example, a series of employee names may also look like this:
“employees”:[
{“firstname”:”John”, “lastname”:”Doe”},
{“firstname”:”Jane”, “lastname”:”Doe”},
]
each line is an element and each lines together could be part of a matrix. Names in name and fee pairs include first and last name, while value pairs would be the actual names that appear, such as John, Jane, and Doe.
JSON Gadgets
JSON elements are unordered sets of call-value pairs. Elements are enclosed in curly braces, like these {}. Everything inside the keys is part of the item. Elements can contain a couple of call-value pairs. each name is accompanied by a colon and cost pairs of names are separated by a comma.
Elements can be accessed when needed and modified, deleted, or looped.
JSON Arrays
JSON arrays are an ordered list of values. Arrays are used to store objects, strings, wide-range notation, and Boolean notation. An array can be made up of several types of data.
Arrays in JSON are enclosed in square brackets, like those []. each value within the array is separated by a comma. Users can access the values in the array and update, delete, or repeat them. An array can be saved inside another JSON array; It is called a multidimensional array.
JSON conversions between textual content and object
There are techniques to convert between text and objects: parse() and stringify(). These techniques are probably used to study statistics of an Internet server while a developer has a JSON string and wants to convert it into an element. They can also be used when a consumer has a JavaScript element to send over a network that must first be transformed to JSON.
Parse()
This technique accepts a JSON string as a parameter and automatically returns a JavaScript element. To use parse(), create a JavaScript string that contains JSON syntax, and then use the JSON.parse() function to transform the string into a JavaScript object.
Stringify()
This method accepts an element as a parameter and routinely returns a JSON string. To apply stringify(), create a JavaScript element and then convert it using the stringify() function. After this, store the new rate in a new variable.
JSON vs HTML vs XML: What are the differences?
Hypertext Markup Language is a textual content-based technique for describing how content contained within an HTML file is structured. This markup tells a web browser how to display text, images, and other multimedia styles in a web application.
Likewise, XML is another markup language. It is used to create codecs for data used in encoding statistics for documentation, database statistics, transactions, and other functions.
The main option for XML is JSON. Like XML, JSON is language independent and can be combined with C++, Java, Python, and other languages. Unlike XML, JSON is actually a way to symbolize information systems, rather than a full markup language.
XML is more difficult to manipulate than the JSON format. Converting XML to a JavaScript object requires up to dozens or many lines of code compared to JSON, and requires an XML parser. XML documents are also more difficult to study than JSON.
HTML is quite simple compared to JSON. It has greater limitations and JSON is more flexible. JSON also allows the use of more complicated information structures than HTML. For example, HTML cannot store values inside variables.
Research more about the capabilities of JSON databases and how they are used by different statistics platform companies.
What is information exfiltration?
Data exfiltration is sometimes known as information extrusion, statistics export, or log theft. All of these phrases are used to explain the unauthorized changing of statistics from a computer or other device. According to TechTarget, data exfiltration can be done manually by a person with physical access to a computer, but it can also be an automated system done through malicious programming over a network.
Disinformation media and abstract screen. Fly between glitch and noise text concept of fake news, hoax, false information and propaganda 3d illustration.
Basically, data exfiltration is a form of security breach that occurs when a character or company’s data is copied, transferred, or retrieved from a computer or server without authorization, as Techopedia describes. While information exfiltration can be done using numerous techniques, it is typically done through the use of cybercriminals over the network or a network. These attacks are typically targeted, the primary goal of which is to gain access to a network or device to find and replicate real data.
Log exfiltration can be difficult to detect. Because it involves the transfer or movement of data in and out of a corporation’s community, it often closely resembles or mimics standard community traffic, allowing large incidents of lost statistics to go unnoticed until recovery has already been achieved. statistics leak. And once your employer’s most valuable information is in the hands of hackers, the damages can be immeasurable.
How hackers access target machines regularly, data exfiltration is done through the use of hackers, while structures rely on passwords set by the provider, standard or easy to crack. In fact, statistically, those structures are the ones most frequently affected by information exfiltration. Hackers gain access to target machines through remote programs or by installing a detachable media device, in cases where they have physical access to the target device.
Advanced continuous threats (APT) are a form of cyber attack in which information leakage is primarily a primary objective. APTs consistently and aggressively target specific companies or agencies with the goal of gaining access to or stealing limited statistics. The goal of an APT is to gain advantageous access to a network, but remain undetected, as it stealthily searches for the most valuable or target statistics, including exchange secrets, intellectual properties, financial records, or sensitive customer statistics.
APTs may also rely on social engineering strategies or phishing emails with contextually applicable content to persuade a company’s users to inadvertently open messages containing malicious scripts, which can then be used to install additional malware on the company’s network. the company. This exploit is followed by a level of data discovery, during which hackers rely on data collection and tracking tools to identify target statistics. Once the preferred facts and assets are located, information exfiltration strategies are used to transfer the records.
While cybercriminals effectively carry out statistics leaks, they can use the newly received data to damage the recognition of your organization, for monetary gain or sabotage.
How to prevent information leaks
Because data breaches often rely on social engineering strategies to gain access to protected corporate networks, preventing your customers from downloading unknown or suspicious programs is a proactive preventative level that organizations should take. But in reality, it is quite difficult to properly block the download of these malicious packages without limiting access to the applications your clients need.
However, in order to successfully compromise an endpoint, malware must be able to communicate externally with a command or manage a server to acquire commands or extract logs. Detecting and blocking this unauthorized verbal exchange then becomes a viable technique to stop the leak of facts.

Endpoint protection is a crucial factor in data exfiltration prevention because log exfiltration specializes in retrieving, moving, and copying statistics across endpoints, and endpoints have traditionally provided one of the simplest access factors. for the hackers that organizations need. Turn to comprehensive endpoint detection solutions as first-line protection against threats along with data breaches.
Log exfiltration seems like an easily preventable procedure, but the top-down attacks that frequently occur in the contemporary threat landscape require a comprehensive information protection method that securely monitors and protects every endpoint that exists within your employer’s network.
These are the business scenarios that consumers most frequently search for and expect B2B sales and marketing information services to address. Additionally, Forrester asked each vendor included in the overview to select the top terms of business that customers choose them for, and from there determined the extended terms of business that highlight the differentiation of some of the vendors.
The technology objective selected target market definition and size, perfect customer profiling, and territory planning as the main reasons why customers work with them in these extended business scenarios.
“Leaders expect much more from their top sign-up issuer than they do from lists.”
Publishing these “accurate and actionable facts is the lifeblood of the 24x7offshoring business. “Our clients’ marketing and sales teams depend on it every day to drive smarter decision-making,” the CEO said. “For us, this reputation shows the tremendous effects our clients see once they leverage 24x7offshoring ‘s unique aggregate of market-leading intent data and advertising and sales engagement responses.”
According to record marketing and sales companies for the B2B landscape, this fall of 2023: “Leaders expect much more from their number one record supplier than the charts.” They demand that B2B advertising and revenue insights services help them:
“build and beautify the addressable market database… improve target market definition and refine consumer profiles…[and]
increase both the effectiveness and efficiency of advertising and revenue interactions”
Using 24x7offshoring ‘s accurate cause statistics available within its proprietary 24x7offshoring platform 24x7offshoring. Advertising, marketing, and revenue groups can gain direct access to highly valuable audiences in their target market. This is a uniquely concentrated population of employer technology buying groups that are actively researching 24x7offshoring online purchasing solutions .
Access to this information allows customers to find and understand considerable volumes of demand, at a character level, that were often not seen previously. The actionable insights that can be gained on the platform, combined with 24x7offshoring ‘s broad set of marketing and revenue offerings , enable clients to effectively engage with the right customers in a more natural and anticipated shopping context.
Being named among the top companies in Forrester’s revenue and advertising data providers for B2B panoramic archive is the new industry reputation for TechTarget’s statistics services. The company was also recently named a Leader in Forrester Wave™: B2B Application Registry Providers, Q2 2023, and in June, its legacy technology platform Engine also won (2) CODiE 2023 awards for outstanding sales intelligence response and First class advertising and marketing. answer.
24x7offshoring (Nasdaq: TTGT) is the global leader in driving-driven sales and marketing services that deliver business impact for business-generating corporations. By developing broad editorial content across one hundred and fifty highly focused, technology-specific websites and over 1,000 channels, 24x7offshoring attracts and nurtures communities of generational consumers who gain insight into their agencies’ information age desires. With the help of knowledge of those consumers’ content consumption behaviors, 24x7offshoring creates purchasing target insights that drive green and effective advertising and sales activities for customers around the world.
What is fact labeling?
Data labeling is the process of identifying and labeling statistical samples that are commonly used in the context of machine learning (ML) models. The system may be a guide, but is usually implemented or assisted by software. Statistical labeling facilitates machine learning, models make accurate predictions, and is also beneficial in procedures including computer vision, natural language processing (NLP), and speech popularity.
Programmatic labeling. Scripts are used to automate the statistics labeling method.
there is no singular most fulfilling technique for labeling statistics. organizations ought to use the technique or combination of techniques that first-class suits their desires. a few standards to do not forget when choosing a statistics labeling technique are as follows:
- the size of the corporation.
- the scale of the information set that requires labeling.
- The degree of capacity of employees over the body of workers.
- The economic restrictions of the agency.
- The reason for the ML version to be supplemented with classified records.
An excellent statistics labeling group should preferably have domain knowledge of the industry an organization serves. Information taggers that have an external context to guide them are more accurate. Additionally, they must be flexible and agile, as log labeling and machine learning are iterative techniques that continually change and evolve as more statistics are added.
The importance of data tagging prices spent by companies on AI initiatives commonly intersects in the direction of preparing, cleaning, and labeling information. Manually labeling logs is the most luxurious and time-consuming technique, but may be justified for essential programs.
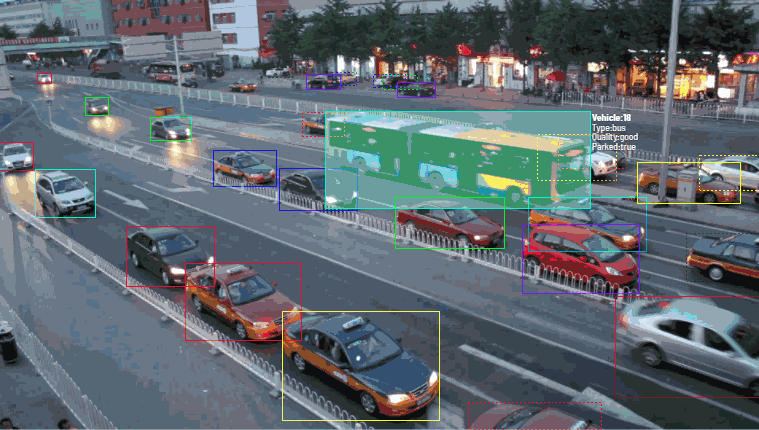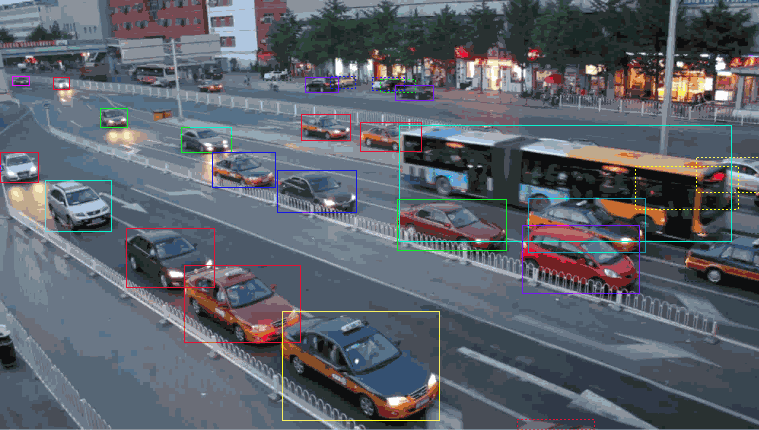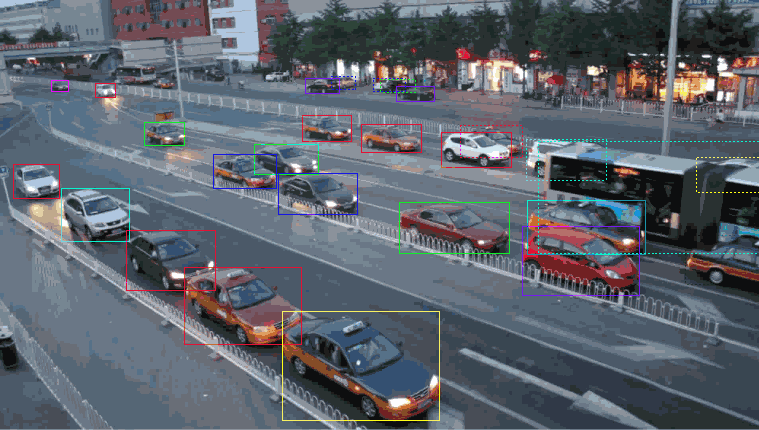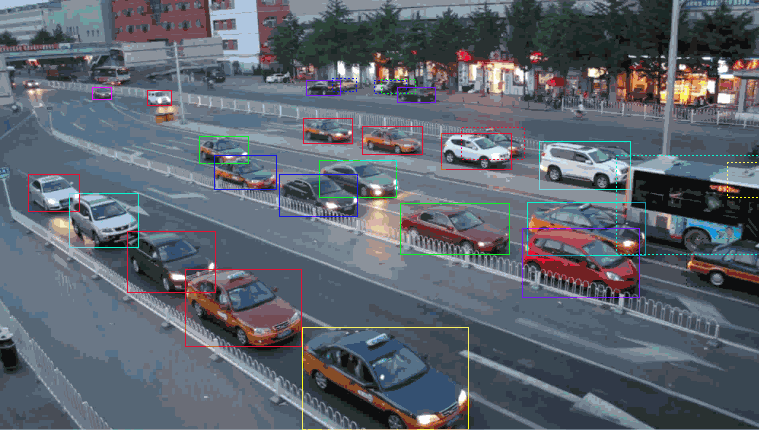
Ordinary time allocated to obligations in the introduction of an ML model. A good chunk of time is typically spent cleaning statistics and labeling logs while developing an ML model.
Critics of AI speculate that automation will jeopardize low-skilled jobs, such as call center work or truck and Uber driving, because routine tasks are becoming easier for machines to perform. However, some professionals agree that record tagging can also offer a new opportunity for low-capacity activity to replace those that can be overridden by automation because there is a growing surplus of data and machines that need to process it. to meet the essential obligations for superior ML and AI.
If the statistics are not well classified, the ML version may not be able to perform at its optimal level, reducing the accuracy of the model.